Yesterday, at my parents’ cabin outside Stockholm, me and my father were having an office session after breakfast. Me procrastinating thesis work, him doing whatever he was doing. At one point he needed to check something on the website of FactWise, a company where he is involved.
The website didn’t appear as it should. The carousel in the footer was broken and the subsequent contact details bar had been pushed off to the side.
The FactWise website is one of the first I’ve made, at least counting those which are still up and running today. Dad had a friend do the design, and I turned the PSDs into a WordPress theme and set it all up on shared hosting. It’s not beautiful but it works – kind of.
When dad showed me the buggy appearance, I was running out of other things to do instead of studying, so I started looking into it immediately. My first guess was that a stylesheet ref was broken. I looked through the Network tab in Firefox Developer Tools to find any 404s, but what I found was something else.
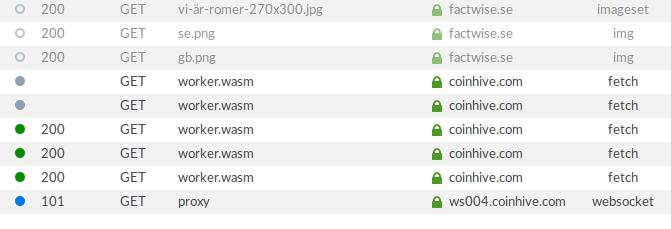
A few lines stood out and called for my attention: resources named “proxy” and “worker.wasm” on a domain called “coinhive.com”. The unfamiliar domain name immediately put my mind on cryptocurrency. After a few minutes googling on the leads, I noticed that the fan in my laptop was running wild. A CPU usage check revealed that a certain Firefox tab was using up all cores. Bitcoin mining.
How was the brain of my laptop being hijacked? How did the intruder gain access to the website, and what kind of access? I closed the tab and continued searching. I looked at the HTML source code, the Developer Tools network tab again, and the WordPress admin pages. The following points sum up my findings:
- The intrusion was likely by brute force (trying different passwords one by one)
- The theme editor was used to add obfuscated js containing binary sequences to footer.php
- Client-side, the js probably fetched and executed cryptocurrency mining code through a proxy at coinhive.com
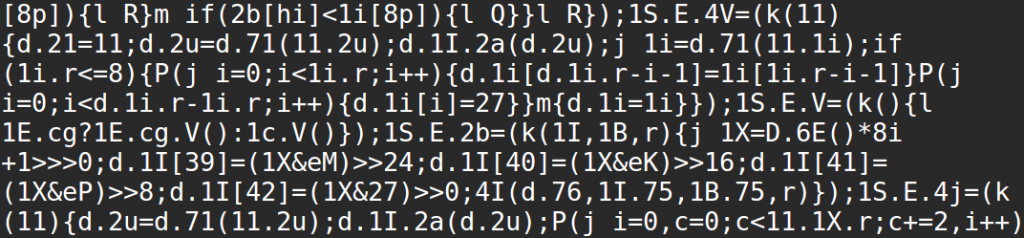
Fortunately, the second step in this procedure had been conducted a bit sloppily. A few lines of HTML were removed from footer.php for no reason. This is what messed up the appearance, which made my dad react and notify me.
So I removed the js and restored the missing lines in footer.php, changed the passwords of the website users and renamed the admin user. While I was at it, I added a favicon and enabled SSL.
I suppose the intruder has broken into and installed the mining code on a vast number of websites, and is making quite a pretty penny with this trick. On my end, I’m actually rather thankful that they didn’t erase the database or redirect visitors to scamming websites.
Leave a Reply